I implemented a custom identity provider for camunda and can use it to log in and run tasks.
But I recently noticed that as a user of group 1, I was also able to run tasks assigned users of group 2. Did I pass too many rights to the user when logging in? Which authorization (APPLICATION, USER, AUTHORIZATION, TASK …) should I take out so that Group1 users are not allowed to run Group2 tasks?
Hi @hassang ,
i dont have a Update -permission for my User. I have only these Permessions:
APPLICATION
USER
GROUP
GROUP_MEMBERSHIP
AUTHORIZATION
FILTER
PROCESS_DEFINITION
TASK
PROCESS_INSTANCE
DEPLOYMENT
DECISION_DEFINITION
TENANT
TENANT_MEMBERSHIP
BATCH
DECISION_REQUIREMENTS_DEFINITION
REPORT
DASHBOARD
OPERATION_LOG_CATEGORY
OPTIMIZE
HISTORIC_TASK
HISTORIC_PROCESS_INSTANCE
SYSTEM
Still run Tasks of Group1 with Users of Group2…
Thanks
These are called resources on which you can grant permissions to users/groups.
Hi @hassang
thanks for your Reply, i found now the Permissions and i change it in Code:
From:
boolean authzExists = authzExists(userId, authorizationService, Authorization.AUTH_TYPE_GRANT,
Permissions.ALL, resource, "*");
if (!authzExists) {
Authorization authz = authorizationService.createNewAuthorization(Authorization.AUTH_TYPE_GRANT);
authz.setUserId(userId);
authz.addPermission(Permissions.ALL);
authz.setResource(resource);
authz.setResourceId("*");
authorizationService.saveAuthorization(authz);
}
To:
boolean authzExists = authzExists(userId, authorizationService, Authorization.AUTH_TYPE_GRANT,
Permissions.ALL, resource, "*");
if (!authzExists) {
Authorization authz = authorizationService.createNewAuthorization(Authorization.AUTH_TYPE_GRANT);
authz.setUserId(userId);
authz.addPermission(Permissions.READ);
authz.addPermission(Permissions.READ_HISTORY);
authz.addPermission(Permissions.READ_INSTANCE);
authz.addPermission(Permissions.READ_TASK);
authz.addPermission(Permissions.TASK_WORK);
authz.addPermission(Permissions.UPDATE);
authz.setResource(resource);
authz.setResourceId("*");
authorizationService.saveAuthorization(authz);
}
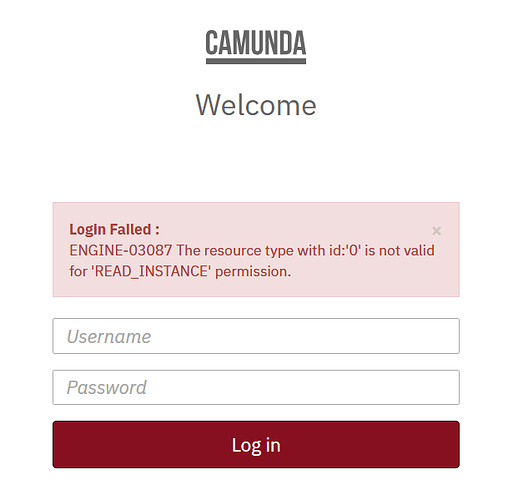
after doing this, i’m not able to Log in any more:
i get the following Error:
What should i do?
I just want that tasks assigned to group2 only runs from group2 users… why is it so difficult?![]()
Last Question :
witch Permissions can i assign to a user for Resources.TASK ?
READ_TASK ?
thanks for your help
Hi @ilyas,
You don’t have to create authorizations programmatically. You can easily do this through the admin app.
Authorizations related to the task are created automatically once the task gets created and as per the task’s configuration (assignee, candidate user(s), candidate group(s)) so no need to create task authorizations.
But you still need to create other authorizations as per your needs
- Application authorizations so users can access
tasklistapp. - Process definition authorizations (for example READ, CREATE_INSTANCE, READ_INSTANCE)
The below doc contains detailed info about authorization
hi @hassang ,
thank your for your support.
my application runs inside Spring-Boot and I built in a Custom Identity Provider for it, so I have to pass the authorization myself.
I deploy my Process also programmatically like this:
DeploymentBuilder builder = repositoryService.createDeployment();
builder.tenantId("TENANT1").addClasspathResource("processes/tenant1/diagramm_mandant.bpmn")
.deploy();
ProcessInstance processInstance = runtimeService.createProcessInstanceByKey("my_approver_process")
.processDefinitionTenantId("TENANT1").execute();
I need to give the autorizations for the process programmatically, how ca i achive that?