Hello All ,
i have upgraded camunda version from 7.11.0 to 7.13.0 and do see 403 error when trying to access teh tasklist page .
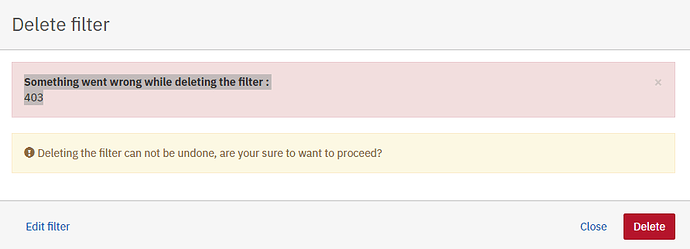
Developer mode response : for loading the filter
{“timestamp”:“2020-08-11T14:34:59.673+00:00”,“status”: 403 ,“error”:“Forbidden”,“message”:"",“path”:"/camunda/api/engine/engine/default/filter/29a51f0c-d8a2-11ea-a0e4-005056b32f3f/list"}
Could someone help me what is the issue here ?
@kamalakannanvkp in version upgrade two things, upgrading the database and upgrading camunda dependency. Have you upgrade both or only db scripts?
Hi @aravindhrs , Yes , i upgraded the camunda dependecy and ran the database upgrade scripts .
The Spring boot componet is up and running fine . I can create instances of the PD . But when i access the tasklist it gives 403 . sample is here
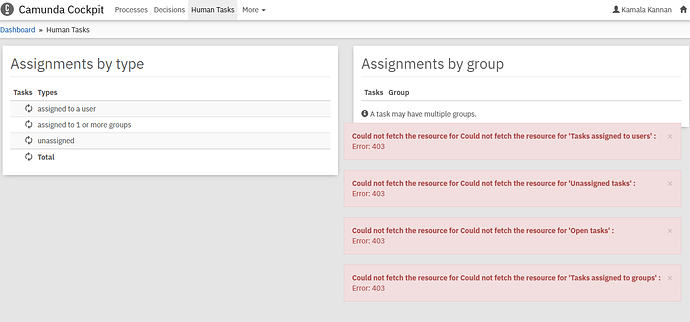
Also, when we tried to access cockpit process instance , i get 403
url + result : {“timestamp”:“2020-08-12T09:19:36.358+00:00”,“status”:403,“error”:“Forbidden”,“message”:"",“path”:/camunda/api/engine/engine/default/process-instance/count}
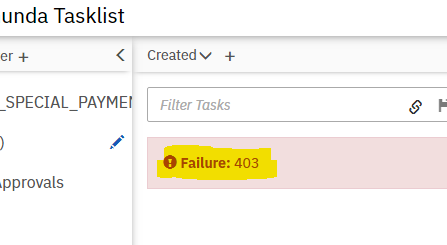
Sample Human Task Error page ::
Also This might help a bit :
we integrated with websso and the already sso-ed session is being used to set the camunda session {i am using the container Based auth strategy} .
Adding few more :
ON loading the camunda main page , it shows my User name , but the groups are not listed , in earlier version i could see the groups for the users are listed in the welcome page
http://localhost:8080/camunda/app/welcome/default/#!/welcome
but after upgrading to new version the same authorized groups are not listed, from teh developer mode i could see the rest-call to retrive the groups are failing with same 403 error
API response :
{“timestamp”:“2020-08-12T11:26:50.882+00:00”,“status”:403,“error”:“Forbidden”,“message”:"",“path”:/camunda/api/engine/engine/default/group}
OPTIONAL , as i am more concerned on the SSO basis
Hi All,
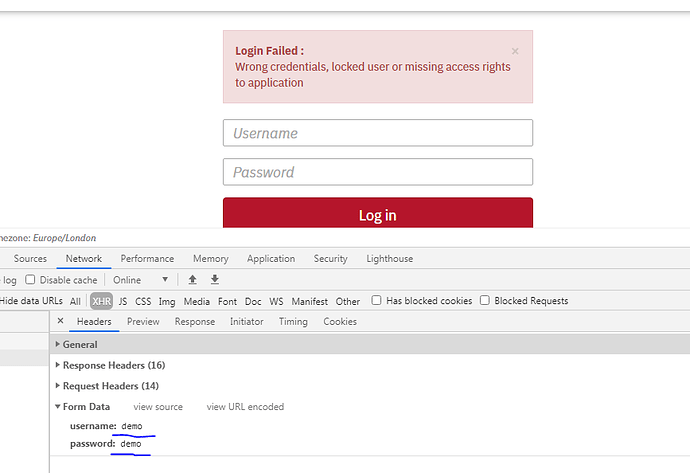
Adding more : i disabled my sso login config and trying to test with usual login page , and it doesnot even accepts the default creds to login
login issue :
Equivalent application.properties config:
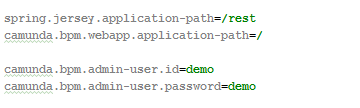
does anyone face this weird issue ?
I am trying to access it from a apache proxy ? is that could be reason , since
http://openshift-route.com/camunda => is my openshift route , i can login with username/pwd
http://apache-proxy.com/camunda ==> accessing the application via apache proxy , i cannot login with the same username/pwd
does any one let me know how to access the app behind a proxy .
OPTIONAL , as i am more concerned on the SSO basis
@aravindhrs @Niall can you suggest ?
Path should be like: /camunda/api/engine/default/process-instance/count
How to change the same , since that is the engine based URL’s.
@aravindhrs :
If above path is wrong , then it must be result in 404 , but not 403 i think.
Also the previous call to fetch all available filters has given some result
URL to fetch list of filters:
Call1:
https://abc.com/camunda/api/engine/engine/default/filter?firstResult=0&maxResults=2000&itemCount=false&resourceType=Task
result is :
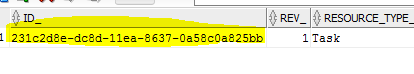
[{“id”:“231c2d8e-dc8d-11ea-8637-0a58c0a825bb”,“resourceType”:“Task”,“name”:" Approvals",“owner”:null,“query”:{“processDefinitionKey”:“APPROVAL_V1”,“taskVariables”:[],“processVariables”:[],“caseInstanceVariables”:[],“orQueries”:[]},“properties”:{“masked”}}]
CAll 2:
The results of above call it is used to load the filter of the above id and gives 403 :
{“timestamp”:“2020-08-12T16:51:54.815+00:00”,“status”:403,“error”:“Forbidden”,“message”:"",“path”:"/camunda/api/engine/engine/default/filter/231c2d8e-dc8d-11ea-8637-0a58c0a825bb/list"}
Oracle Def:
ACT_RU_FILTER
::
@kamalakannanvkp - We are also facing the exactly same issue. We have used ContainerBasedAuthenticationProvider and integrated with LDAP to authenticate the user. But after authentication the user authorization is not working. We are getting 403 forbidden error.
Is your issue resolved? If yes, Could you please guide us the way forward.
Thanks!!
Hi, in my case it was X-XSRF-TOKEN was missed when i added/routed with https over httpd servers, so it did not work .
@kamalakannanvkp -
So for us the user is getting authenticated using the Spring Security Framework. And we also get the user details like username, Group in “AuthenticationResult” object.
So when we login through Spring login page then it directly takes us to the main Camunda welcome page. When we try to create a user\group or try to access the tasklist then we are getting “403” forbidden error.
We also inspected the calls on chrome browser and could see in the user creation calls the XSRF token is not getting passed as part of request-headers.
Could this be the problem? How can we fix it. Please advise.
Thanks!
Looks like you also ran into the same problem as i had . We were able to authenticate but not view the tasklist page . I am not sure exactly whats being caused in your case . Does it work in http mode with hardcoded username pwd? we can compare the calls as like how i debugged
@kamalakannanvkp -
Yes when we used inMemoryUserDetailsManager and passed the “demo” user and “demo” password it worked for us. And our communication is over Http only. We are not using https.
Thanks!
@kamalakannanvkp -
You are right. We seem to have exactly same problem which you have already fixed. It would be really helpful if you can let us know the steps to follow.
Thanks!
I have faced the exact same issue as the OP. We also have SSO configured and I was facing this issue only on POST requests. This is a telltale sign of CSRF issue, so I disabled CSRF in my Spring security config for the requests starting with camunda/** and things are working fine now. But, this is not a solution as disabling CSRF protection is a security hole. I will update once I find the real solution.
Hi, please check the XSRF token as well
Yeah, so after debugging the failure Spring is having, I found that spring is expecting a X-CSRF-TOKEN header but the requests are sending a X-XSRF-TOKEN header. I am looking around to handle this gracefully but if anyone has some ideas, do pitch in.
I found it. You need to set the CookieCsrfTokenRepository in Spring security config. See the docs at https://docs.spring.io/spring-security/site/docs/5.0.x/reference/html/csrf.html#csrf-cookie
4 Likes
Thank You. It worked.
httpSecurity.csrf()
.csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse());