Hi,
Been testing out the ‘Connect to an existing Keycloak Instance’ documentation (Connect to an existing Keycloak instance | Camunda Platform 8 Docs) provided as part of Camunda 8.1. I created a standalone C8 identity service in Kubernetes using camunda/identity:8.1.2 to connect to my organisation’s existing keycloak instance.
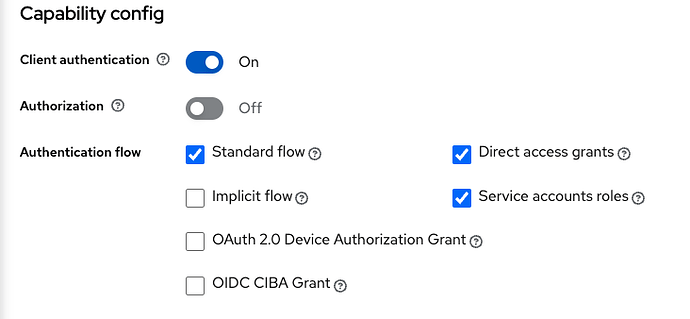
As we were using keycloak v19, the UI for configuring the camunda-identity client is slightly different, however I believe it is identical to what is described in the doc.
As described in the document, I have set the following environment variables, keeping in mind that the realm path for keycloak 19 is slightly different:
- name: KEYCLOAK_URL
value: https://[KEYCLOAK_HOST]
- name: IDENTITY_AUTH_PROVIDER_ISSUER_URL
value: https://[KEYCLOAK_HOST]/realms/camunda-platform
- name: IDENTITY_CLIENT_ID
value: camunda-identity
- name: IDENTITY_CLIENT_SECRET
value: .......
- name: KEYCLOAK_REALM
value: camunda-platform
Note that this step of the documentation was followed:
However, I was getting a 401 error.
$ k logs -n dev c8-identity-56c48c9d5-gqwc4 --previous
...
2022-10-19 01:00:49.450 ERROR 1 --- [ main] i.c.i.i.k.c.KeycloakConfiguration : Failure #6. Unable to connect to Keycloak.
2022-10-19 01:00:49.450 ERROR 1 --- [ main] i.c.i.i.k.c.KeycloakConfiguration : javax.ws.rs.NotAuthorizedException: HTTP 401 Unauthorized
Despite the manual verification of the client working as expected:
$ curl -d "client_id=camunda-identity" -d "client_secret=......" -d "grant_type=client_credentials" "https://[KEYCLOAK_HOST]/realms/camunda-platform/protocol/openid-connect/token"
{"access_token":"...","expires_in":300,"refresh_expires_in":0,"token_type":"Bearer","not-before-policy":0,"scope":"email profile"}
Checking the logs for keycloak itself, it looks like C8 Identity is still attempting to log into using the master realm using the KEYCLOAK_SETUP_* environment variables (i.e. new keycloak instance and realm), and the password grant type, rather than set up keycloak through my existing instance/realm.
2022-10-19 00:47:41,688 WARN [org.keycloak.events] (executor-thread-161) type=LOGIN_ERROR, realmId=master, clientId=admin-cli, userId=null, ipAddress=10.xx.xx.xx, error=invalid_client_credentials, grant_type=password
Is there something I’m doing incorrectly here? Would really like to get C8 identity connected to an existing keycloak instance/realm.