Continuing my journey to try to get Camunda 8 self-hosted on Google Cloud with Google Kubernetes engine, I made a lot of progress and most of the stuff, from pods to ingress, seems to be working now.
Unfortunately, I fail to login when I open Tasklist oder Operate as the browser gets stuck in a redirect loop between Operate and Keycloak. I’m out of ideas of what might cause this.
I have setup an combined ingress in GKE that I also now have setup with a valid, non-self-signed certificate.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: camunda-ingress
annotations:
kubernetes.io/ingress.global-static-ip-name: "my-ip"
ingress.gcp.kubernetes.io/pre-shared-cert: "my-cert"
spec:
rules:
- http:
paths:
- path: /operate
pathType: Prefix
backend:
service:
name: camunda-operate
port:
number: 80
- path: /auth
pathType: Prefix
backend:
service:
name: camunda-keycloak
port:
number: 80
In my helm values file I configured the redirect URIs accordingly:
global:
identity:
auth:
publicIssuerUrl: "https://mydomain.com/auth/realms/camunda-platform"
operate:
redirectUrl: "https://mydomain.com/operate/operate"
My identityKeycloak section is also not much to write home about:
identityKeycloak:
service:
annotations:
cloud.google.com/neg: '{"ingress": true}'
readinessGates:
- conditionType: "cloud.google.com/load-balancer-neg-ready"
I did not more adaptations to anything related to Identity or Keycloak.
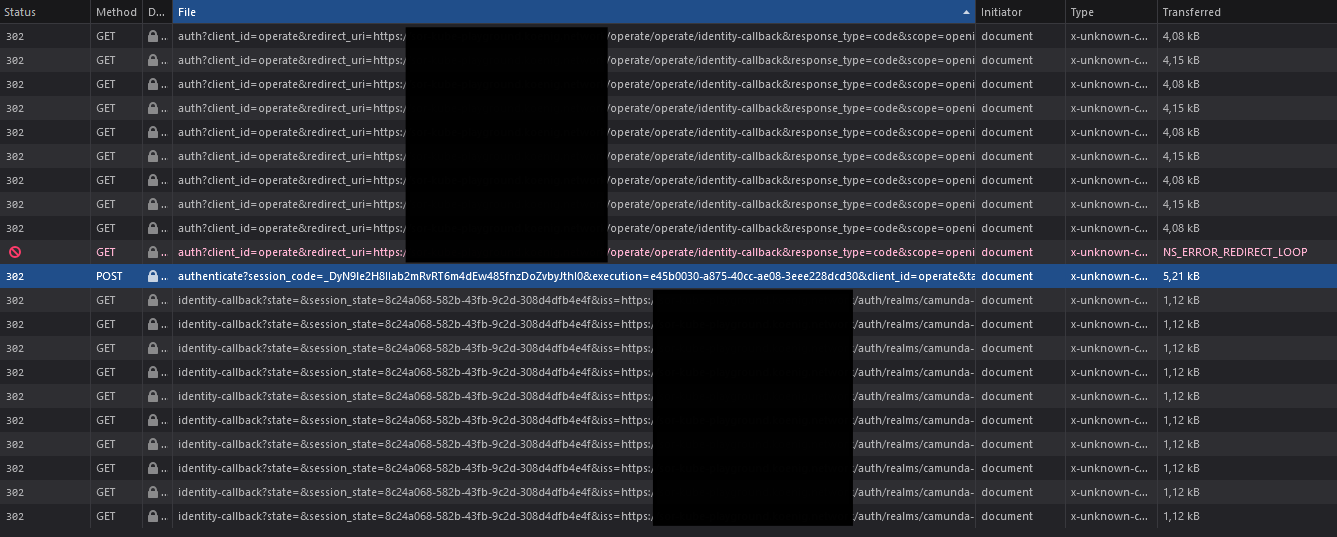
When I open Operate, I get redirected correctly to Keycloak for the login page. I can login and the login seemingly is successful as I get the redirect after that and I can see cookies from Keycloak are set. But it now goes in an infinite redirect loop until the browser detects the infinite loop.
What could be causing this? I even tried to put Keycloak on a separate non-combined ingress as I read somewhere that combined ingress might cause issues (althought only non-HTTPS) but it did not change anything.
I’m puzzled of where I could even start to look for the cause of this.
That’s how it looks like in the browsers network tab (for some reason the requests do not seem to be in actual order):
Can anybody point me in the right direction of what might be causing this?
Update: I now see errors in operate logs about not being authenticated when this happens:
io.camunda.webapps.controllers.WebappsRequestForwardManager - Requested path /operate/identity-callback, but not authenticated. Redirect to /api/login
Hmmm. But why. Login succeeds. Redirect happens. Is it the wrong redirect endpoint of Operate?