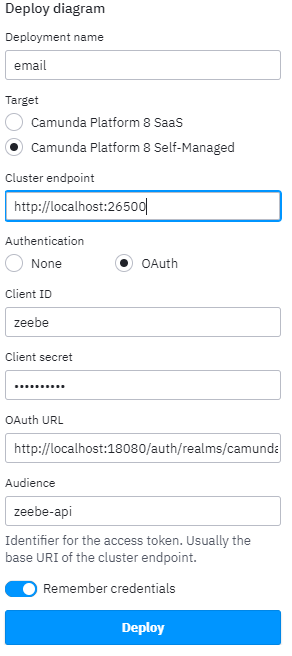
I am trying to evaluate camunde. I am running the system on a self-hosted kubernetes cluster. the application is deployed via helm chart. (whith minimal changes). All important ports are forwarded from MY local PC to the camunda processes. I know that everything is operational as i am able to deploy and run processes via the modeler (on my local pc) via these settings:
BUT i have problem to get the Spring-Boot-Email-Example to run. (connection to zeebe)
In the documentation is mentioned to do it like this
zeebe.client.broker.gatewayAddress=127.0.0.1:26500
zeebe.client.security.plaintext=true
but of course it does not work because oauth is not configured and the server “misses” the bearer token ![]()
So … there does not seem to be a “documented” way to pass the authorization information via application .properties/yaml for the self hosted camunda.
I am willing to overwrite some Beans to pass my own OAuthCredentialsProvider into the system. but i did not found the “hook” to do it for the Spring-example (which uses a ZeebeClientLifecycle instead of a plain ZeebeClient).
Thank you for any hints