Hi there,
I am trying to install the latest release and having trouble almost at the last few steps.
Initially tested with creating the elasticsearch as part of Camunda installation and that worked nice. I am now trying to use an existing elasticsearch, and facing this error.
(camunda-platform - 12.0.0-alpha4)
helm values yaml file:
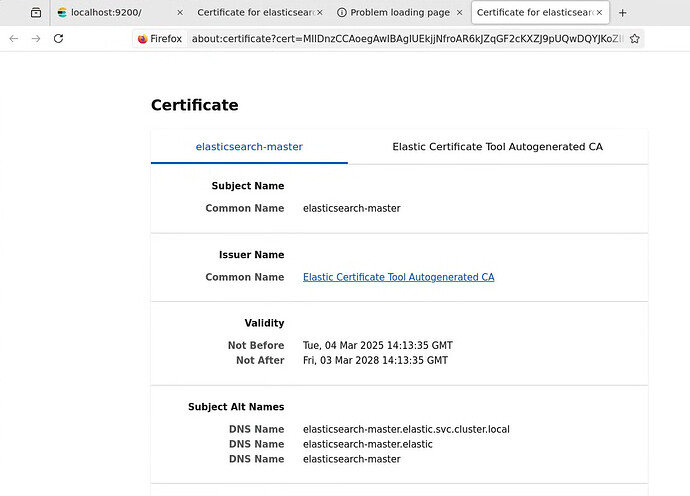
I am supplying the elasticsearch hostname as “elasticsearch-master.elastic.svc.cluster.local” - however the self signed certificated generated during the elasticsearch install uses. just this name “elasticsearch-master”.
Using only “https://elasticsearch-master:9200” resulted in connection refused error. I opened a shell terminal and noticed that only full name gets recognised.
The elasticsearch and Kibana are installed in “elastic” namespace, whereas Camunda is in another namespace.
I followed the steps given here to define a secret along with the certificate file.
This is certainly not a Camunda app issue, more like a configuration elements issue. Thought of checking if anyone encountered this.
From the initial analysis, it seems like disabling the hostname verification will circumvent this error. Is there any way to configure this via the helm values yaml?
Please advise.
(camunda-platform - 12.0.0-alpha4)
The “pod: task list app” shows below error in the logs. Most of the components are up except for the web apps (task list, operate, optimise).
io.camunda.tasklist.es.ElasticsearchConnector - Retrying #12 connect to Elasticsearch at https://elasticsearch-master.elastic.svc.cluster.local:9200 due to ElasticsearchException[java.util.concurrent.ExecutionException: javax.net.ssl.SSLPeerUnverifiedException: Host name ‘elasticsearch-master.elastic.svc.cluster.local’ does not match the certificate subject provided by the peer (CN=elasticsearch-master)]; nested: ExecutionException[javax.net.ssl.SSLPeerUnverifiedException: Host name ‘elasticsearch-master.elastic.svc.cluster.local’ does not match the certificate subject provided by the peer (CN=elasticsearch-master)]; nested: SSLPeerUnverifiedException[Host name ‘elasticsearch-master.elastic.svc.cluster.local’ does not match the certificate subject provided by the peer (CN=elasticsearch-master)];
yaml file snippet:
global:
elasticsearch:
enabled: true
external: true
tls:
enabled: true
existingSecret: elastic-jks
auth:
username: elastic
password: makelabs
url:
protocol: https
host: elasticsearch-master.elastic.svc.cluster.local
port: 9200
clusterName: elasticsearch
prefix: zeebe-record