Hi @ad_sahota ,
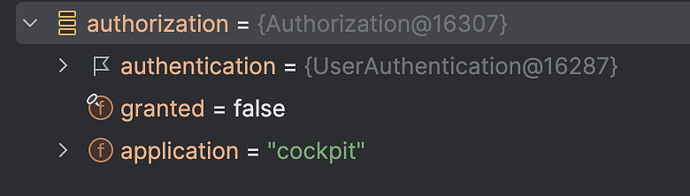
Thank you for the help. Now that I am able to resolve the authentication value and all required authorisations (group, tenants) are present, I don’t get any exception in logs. But the login to Camunda cockpit is still blocked and I see the usual login page of Camunda instead of being logged in to access cockpit.
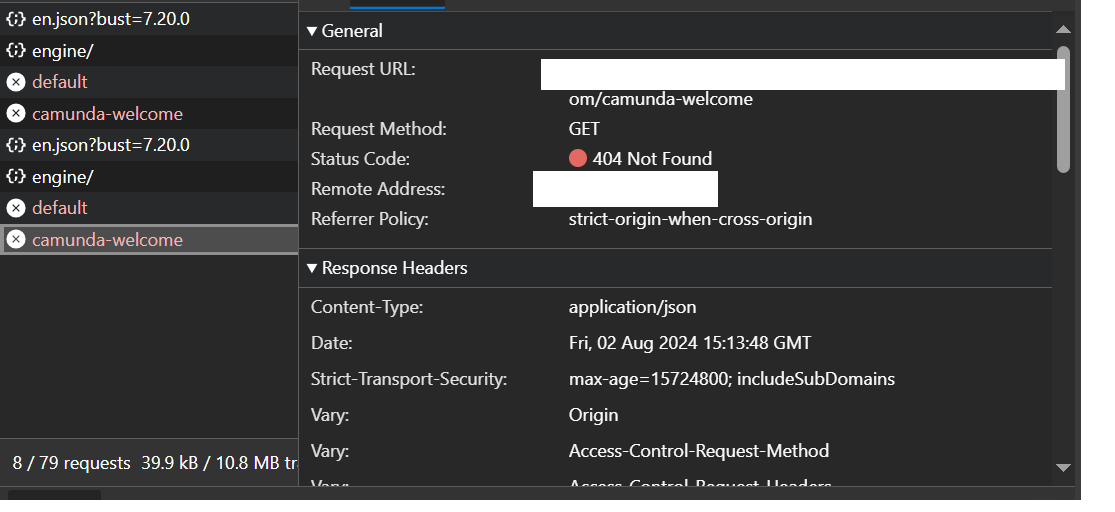
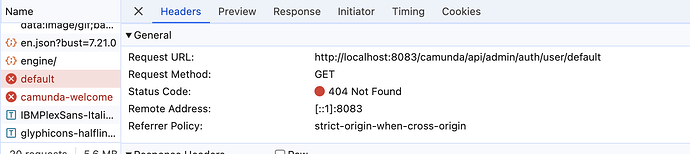
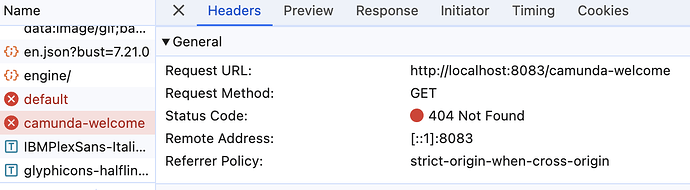
The logs I am getting now as below and few error that I have highlighted where GET /camunda-welcome gives 404.
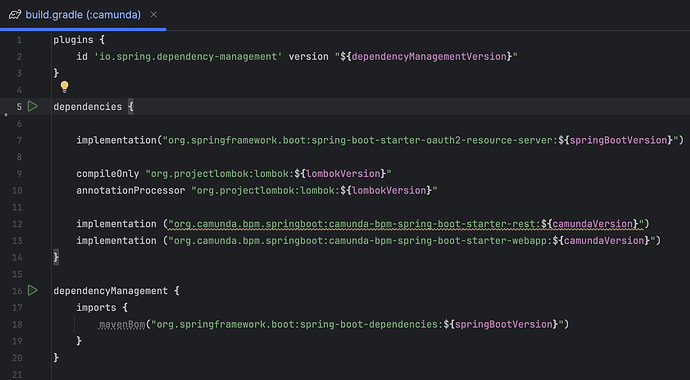
Can you please suggest if I am missing anything that I need to add.
2024-08-02 11:12:09,168 DEBUG anwesha [http-nio-8083-exec-7] o.s.s.w.FilterChainProxy Securing GET /camunda/api/engine/engine/
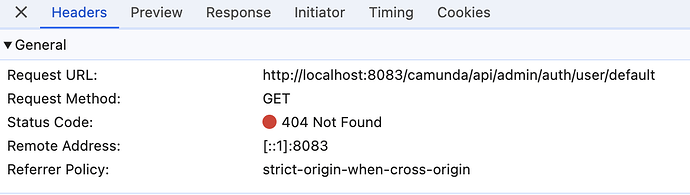
2024-08-02 11:12:09,168 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.w.FilterChainProxy Securing GET /camunda/api/admin/auth/user/default
2024-08-02 11:12:09,169 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.o.s.r.a.JwtAuthenticationProvider Authenticated token
2024-08-02 11:12:09,169 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.o.s.r.w.a.BearerTokenAuthenticationFilter Set SecurityContextHolder to BearerTokenAuthentication [Principal=org.springframework.security.oauth2.core.DefaultOAuth2AuthenticatedPrincipal@686a0ab5, Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=0:0:0:0:0:0:0:x, SessionId=null], Granted Authorities=[SCOPE_internal, SCOPE_public]]
2024-08-02 11:12:09,169 DEBUG anwesha [http-nio-8083-exec-7] o.s.s.o.s.r.w.a.BearerTokenAuthenticationFilter Set SecurityContextHolder to BearerTokenAuthentication [Principal=org.springframework.security.oauth2.core.DefaultOAuth2AuthenticatedPrincipal@11961a52, Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=0:0:0:0:0:0:0:x, SessionId=xxx], Granted Authorities=[SCOPE_internal, SCOPE_public]]
2024-08-02 11:12:09,170 DEBUG anwesha [http-nio-8083-exec-7] o.s.s.w.FilterChainProxy Secured GET /camunda/api/engine/engine/
2024-08-02 11:12:09,170 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.w.FilterChainProxy Secured GET /camunda/api/admin/auth/user/default
2024-08-02 11:12:10,321 DEBUG anwesha [http-nio-8083-exec-5] o.s.w.s.DispatcherServlet GET "/camunda/app/cockpit/locales/en.json?bust=7.21.0", parameters={masked}
2024-08-02 11:12:10,321 DEBUG anwesha [http-nio-8083-exec-8] o.s.w.s.DispatcherServlet GET "/camunda/assets/IBMPlexSans-Italic.woff?bust=7.21.0", parameters={masked}
2024-08-02 11:12:10,322 DEBUG anwesha [http-nio-8083-exec-5] o.s.w.s.h.SimpleUrlHandlerMapping Mapped to ResourceHttpRequestHandler [classpath [META-INF/resources/webjars/camunda/app/]]
2024-08-02 11:12:10,322 DEBUG anwesha [http-nio-8083-exec-8] o.s.w.s.h.SimpleUrlHandlerMapping Mapped to ResourceHttpRequestHandler [classpath [META-INF/resources/webjars/camunda/assets/]]
2024-08-02 11:12:10,326 DEBUG anwesha [http-nio-8083-exec-8] o.s.w.s.DispatcherServlet Completed 200 OK
2024-08-02 11:12:10,326 DEBUG anwesha [http-nio-8083-exec-5] o.s.w.s.DispatcherServlet Completed 200 OK
2024-08-02 11:12:10,327 INFO anwesha [http-nio-8083-exec-5] c.d.p.l.f.RequestLogFilter {requestURI=/camunda/app/cockpit/locales/en.json, httpMethod=GET, queryString=bust=7.21.0, responseCode=200}
2024-08-02 11:12:10,327 INFO anwesha [http-nio-8083-exec-8] c.d.p.l.f.RequestLogFilter {requestURI=/camunda/assets/IBMPlexSans-Italic.woff, httpMethod=GET, queryString=bust=7.21.0, responseCode=200}
2024-08-02 11:12:10,528 DEBUG anwesha [http-nio-8083-exec-9] o.s.w.s.DispatcherServlet GET "/camunda/assets/glyphicons-halflings-regular.woff2?bust=7.21.0", parameters={masked}
2024-08-02 11:12:10,528 DEBUG anwesha [http-nio-8083-exec-9] o.s.w.s.h.SimpleUrlHandlerMapping Mapped to ResourceHttpRequestHandler [classpath [META-INF/resources/webjars/camunda/assets/]]
2024-08-02 11:12:10,531 DEBUG anwesha [http-nio-8083-exec-9] o.s.w.s.DispatcherServlet Completed 200 OK
2024-08-02 11:12:10,531 INFO anwesha [http-nio-8083-exec-9] c.d.p.l.f.RequestLogFilter {requestURI=/camunda/assets/glyphicons-halflings-regular.woff2, httpMethod=GET, queryString=bust=7.21.0, responseCode=200}
2024-08-02 11:12:10,552 INFO anwesha [http-nio-8083-exec-7] c.d.p.l.f.RequestLogFilter {requestURI=/camunda/api/engine/engine/, httpMethod=GET, responseCode=200}
2024-08-02 11:12:10,735 INFO anwesha [http-nio-8083-exec-4] c.d.p.l.f.RequestLogFilter {**requestURI=/camunda/api/admin/auth/user/default, httpMethod=GET, responseCode=404}**
2024-08-02 11:12:10,742 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.w.FilterChainProxy Securing GET /error
2024-08-02 11:12:10,743 DEBUG anwesha [http-nio-8083-exec-4] o.s.s.w.FilterChainProxy Secured GET /error
2024-08-02 11:12:10,743 DEBUG anwesha [http-nio-8083-exec-4] o.s.w.s.DispatcherServlet "ERROR" dispatch for GET "/error", parameters={}
2024-08-02 11:12:10,743 DEBUG anwesha [http-nio-8083-exec-4] o.s.w.s.m.m.a.RequestMappingHandlerMapping Mapped to org.springframework.boot.autoconfigure.web.servlet.error.BasicErrorController#error(HttpServletRequest)
2024-08-02 11:12:10,758 DEBUG anwesha [http-nio-8083-exec-4] o.s.w.s.m.m.a.HttpEntityMethodProcessor Using 'application/json', given [application/json, text/plain, */*] and supported [application/json, application/*+json]
2024-08-02 11:12:10,758 DEBUG anwesha [http-nio-8083-exec-4] o.s.w.s.m.m.a.HttpEntityMethodProcessor **Writing [{timestamp=Fri Aug 02 11:12:10 UTC 2024, status=404, error=Not Found, path=/camunda/api/admin/auth/u (truncated)...]**
2024-08-02 11:12:10,764 DEBUG anwesha [http-nio-8083-exec-4] o.s.w.s.DispatcherServlet Exiting from "ERROR" dispatch, status 404
2024-08-02 11:12:10,764 INFO anwesha [http-nio-8083-exec-4] c.d.p.l.f.RequestLogFilter {requestURI=/error, httpMethod=GET, responseCode=404}
2024-08-02 11:12:10,783 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.w.FilterChainProxy Securing GET /camunda-welcome
2024-08-02 11:12:10,785 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.o.s.r.a.JwtAuthenticationProvider Authenticated token
2024-08-02 11:12:10,786 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.o.s.r.w.a.BearerTokenAuthenticationFilter Set SecurityContextHolder to BearerTokenAuthentication [Principal=org.springframework.security.oauth2.core.DefaultOAuth2AuthenticatedPrincipal@16de548e, Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=0:0:0:0:0:0:0:x, SessionId=xxx], Granted Authorities=[SCOPE_internal, SCOPE_public]]
2024-08-02 11:12:10,787 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.w.a.s.ChangeSessionIdAuthenticationStrategy Changed session id from xxx
2024-08-02 11:12:10,788 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.w.FilterChainProxy Secured GET /camunda-welcome
2024-08-02 11:12:11,407 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.DispatcherServlet GET "/camunda-welcome", parameters={}
2024-08-02 11:12:11,408 WARN anwesha [http-nio-8083-exec-10] **o.s.w.s.PageNotFound No mapping for GET /camunda-welcome**
2024-08-02 11:12:11,409 WARN anwesha [http-nio-8083-exec-10] **o.s.w.s.PageNotFound No endpoint GET /camunda-welcome.**
2024-08-02 11:12:11,410 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.m.s.DefaultHandlerExceptionResolver Resolved [org.springframework.web.servlet.NoHandlerFoundException: No endpoint GET /camunda-welcome.]
2024-08-02 11:12:11,410 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.DispatcherServlet Completed 404 NOT_FOUND
2024-08-02 11:12:11,411 INFO anwesha [http-nio-8083-exec-10] c.d.p.l.f.RequestLogFilter **{requestURI=/camunda-welcome, httpMethod=GET, responseCode=404}**
2024-08-02 11:12:11,411 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.w.FilterChainProxy Securing GET /error
2024-08-02 11:12:11,412 DEBUG anwesha [http-nio-8083-exec-10] o.s.s.w.FilterChainProxy Secured GET /error
2024-08-02 11:12:11,412 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.DispatcherServlet "ERROR" dispatch for GET "/error", parameters={}
2024-08-02 11:12:11,412 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.m.m.a.RequestMappingHandlerMapping Mapped to org.springframework.boot.autoconfigure.web.servlet.error.BasicErrorController#error(HttpServletRequest)
2024-08-02 11:12:11,413 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.m.m.a.HttpEntityMethodProcessor Using 'application/json', given [application/json, text/plain, */*] and supported [application/json, application/*+json]
2024-08-02 11:12:11,413 DEBUG anwesha [http-nio-8083-exec-10] o.s.w.s.m.m.a.HttpEntityMethodProcessor Writing [{timestamp=Fri Aug 02 11:12:11 UTC 2024, status=404, error=Not Found, path=/camunda-welcome}]